Practical Guide Implementing
Attack Surface Management
Organizations worldwide face unprecedented challenges as their cyber asset inventories jumped 133% in just one year. Attack surface management has become more complex than ever. Most organizations say managing their attack surfaces is harder now than it was two years ago. Security teams can't keep up with more than 100 new vulnerabilities popping up each day and ransomware attacks shooting up 126% in early 2025.
Attack surface management helps organizations stay ahead of threats. It's a systematic way to find, classify, and track all external-facing digital assets that attackers might target. The main goal is simple - organizations need to see their systems through an attacker's eyes and focus their defenses where they matter most. Organizations can better protect themselves from cyber attacks when they actively manage their attack surface. This means constantly finding assets, checking for vulnerabilities, and focusing on the biggest risks.
Several key factors determine the right external attack surface management solution. These include how big your organization is, what asset records you already have, your current monitoring setup, and your unique security challenges. Cyberattacks surged 47% worldwide in early 2025, which makes having the right attack surface management tools and strategies crucial.
This piece shows you the key steps to set up attack surface management. You'll learn everything from mapping your attack surface to tracking performance and creating ongoing improvement cycles.
Mapping and Scoping Your Attack Surface
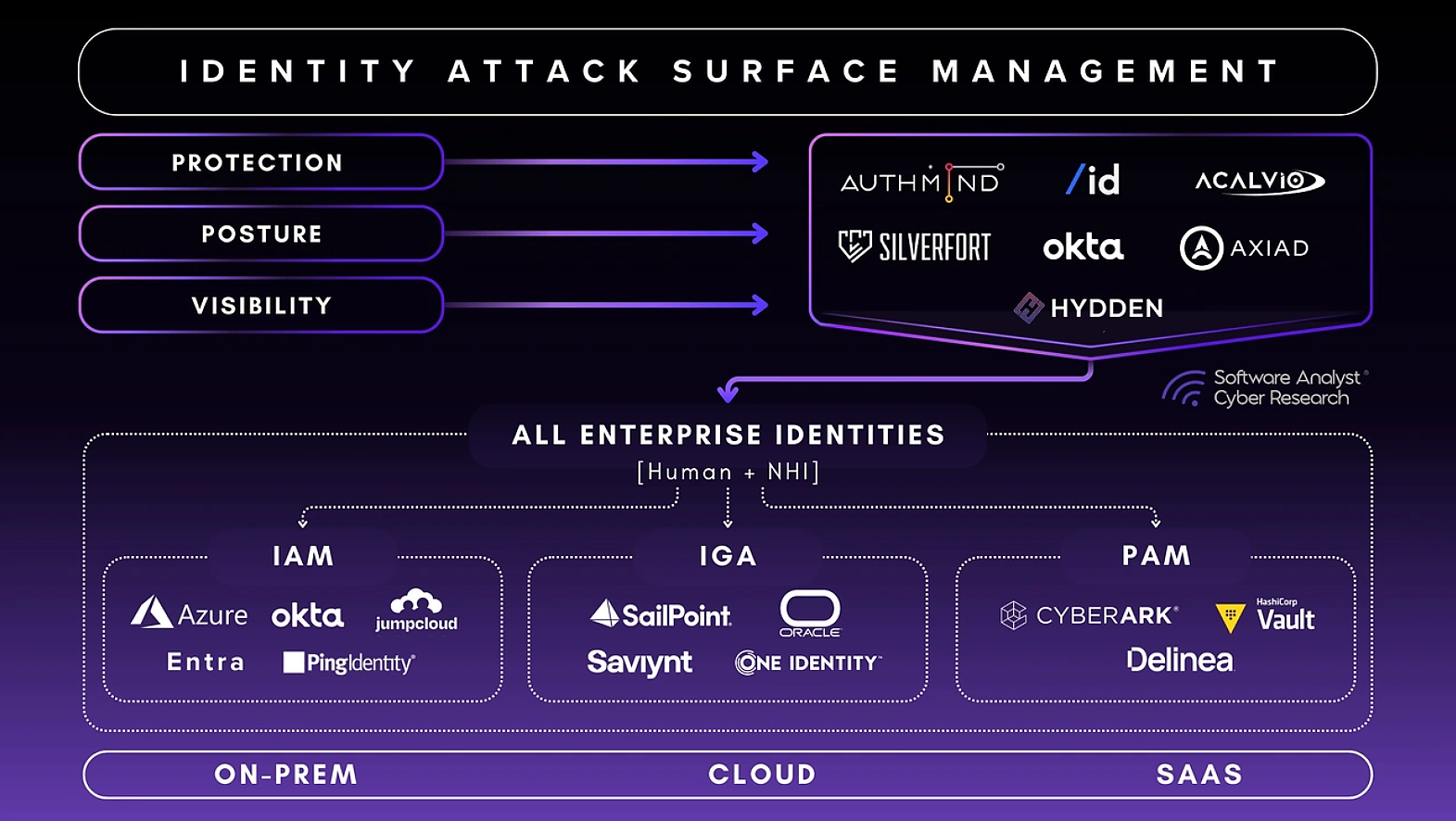
Image Source: Software Analyst Cyber Research - Substack
Organizations can't defend what they can't see. The attack surface represents all potential entry points where unauthorized users can access systems and steal data. Research shows enterprises remain unaware of about 40-60% of their attack surface. This creates major blind spots in their security setup.
What is attack surface and why it matters
The attack surface represents every possible attack vector that hackers can use to break into a network or system. It has everything from exposed servers and unpatched software to misconfigured cloud services and open ports. Attack surfaces fall into three main categories:
- Digital attack surface: Hardware, software, network interfaces, APIs, and cloud services exposed to the internet make up this surface
- Physical attack surface: Laptops, mobile phones, and USB drives that attackers can physically access from this category
- Social engineering attack surface: People who might fall victim to phishing or other manipulation tactics create this surface
Organizations need to understand their attack surface completely. Without visibility into exposed assets, they work blindly and react to incidents instead of preventing them. Modern cyber threats make securing these entry points crucial.
How to discover known and unknown assets
Asset discovery starts with clear scope boundaries for systems, networks, and applications that need examination. This creates a complete baseline infrastructure map and identifies valuable "crown jewel" assets that need priority protection.
Shadow IT, orphaned applications, and rogue assets create the riskiest parts of an attack surface. Tools that run automatically help spot both known assets (servers, devices, applications) and hidden ones (forgotten systems, misconfigured services).
Asset discovery should list all possible attack vectors with their location, severity, and exploitation methods. Risk heatmaps emerge when this information appears in diagrams or dashboards.
What is external attack surface management
External Attack Surface Management (EASM) focuses on finding and tracking internet-facing assets that could become entry points. This system constantly scans for vulnerabilities, misconfigurations, and exposed credentials across public-facing digital assets.
EASM uses automated discovery to map external-facing infrastructure and highlight weak spots that attackers might target. Security teams can move from reactive to proactive defense by finding and fixing vulnerabilities before attackers exploit them.
Building a Risk-Based ASM Strategy
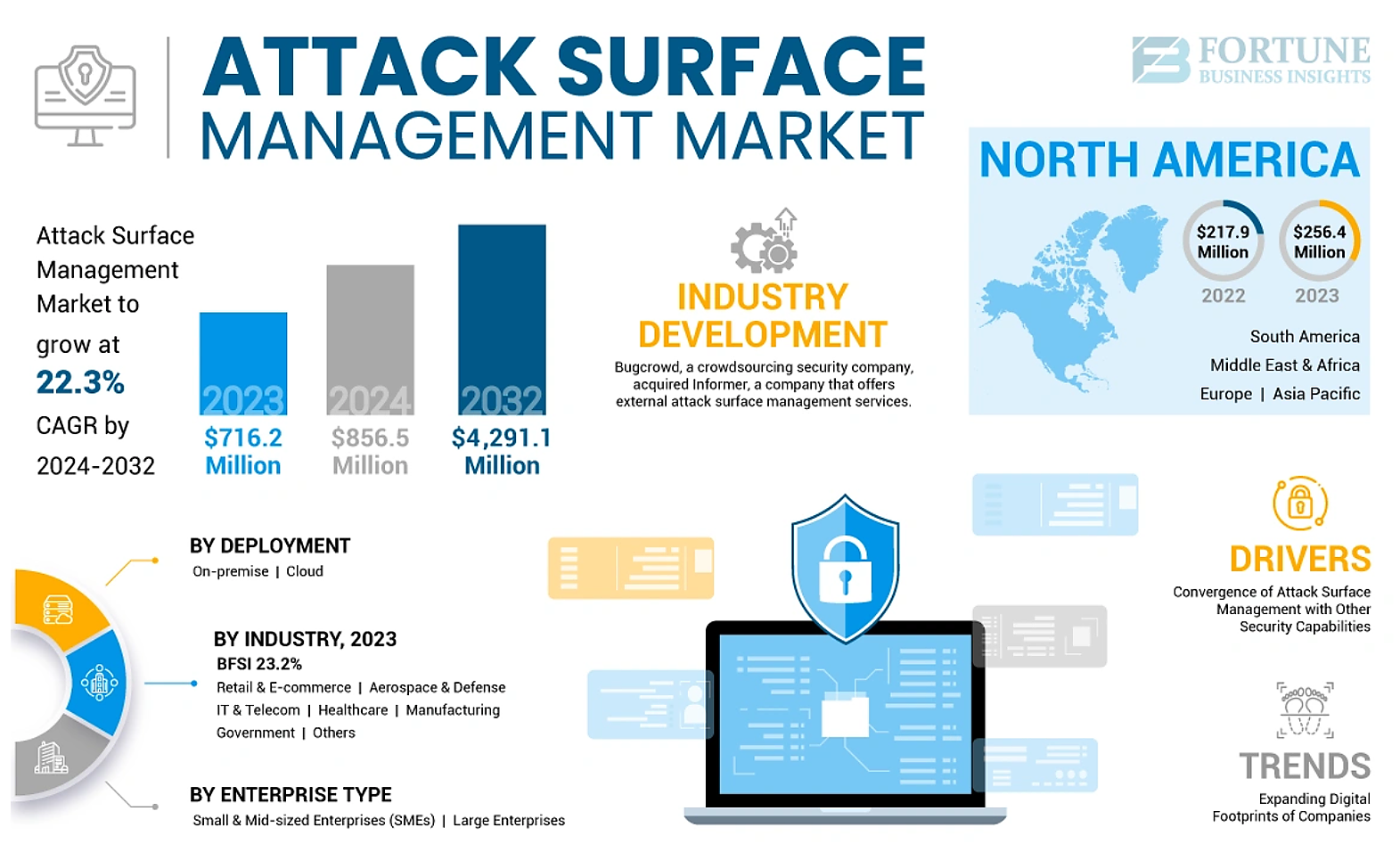
Image Source: Fortune Business Insights
Attack surface management works best when teams take a smart approach to assessing risks. Security teams should not just find assets but create a well-laid-out system to evaluate and respond.
Prioritizing assets based on business effect
A production database containing customer data requires far more protection than a staging environment that holds test data. Security teams can better use their resources when they know which assets keep critical business applications running. Your security strategy must acknowledge that digital assets have different values. Businesses must sort and prioritize assets based on their business context and what could happen if someone compromises them. This means understanding:
- How sensitive the data is and its classification
- How exposed systems are to potential threats
- How vital these systems are to business operations
- The money at risk if they are breached
A production database containing customer data requires much more protection.
Making decisions based on threat intelligence
Threat intelligence provides essential information about possible attackers and their tactics, transforming basic asset data into relevant security information. Without this context, security teams frequently become overloaded with notifications and focus on little issues while leaving larger vulnerabilities unfixed.
Understanding who might target particular assets and why, based on actual threat scenarios, helps teams prioritize their work more effectively. While providing prompt updates on particular dangers, it also aids in concentrating testing on probable attack patterns.
Creating risk scores and tolerance levels
Companies should set clear limits about what risks they accept. Risk scoring works in two steps: identifying relevant risks and giving them scores based on urgency and how bad things could get.
The Common Vulnerability Scoring System (CVSS) helps the industry rate vulnerabilities on a scale from 0.0 to 10.0. The severity calculations multiply financial effect by how likely an attack is, which shows how big the threat really is.
Companies can track their security status over time by watching these scores constantly. This helps them spot which risks need immediate action and shows when their fixes have worked.
Implementing and Operationalizing ASM
ASM tools must be carefully selected and integrated into existing security processes for successful implementation. The ASM market will grow at a compound annual rate exceeding 30% through 2030. This rapid growth makes choosing the right tools more challenging.
Choosing the right attack surface management tools
Organizations should focus on platforms that offer continuous discovery features for hybrid and multicloud environments. Good tools give detailed visibility through multiple techniques like passive reconnaissance, active scanning, and DNS monitoring. Organizations need daily scans at minimum. Companies with changing infrastructure should aim for immediate monitoring as the best practice.
Integrating ASM into existing security workflows
ASM investments become more valuable when they merge with existing security infrastructure. The best solutions easily connect with SIEM, SOAR, vulnerability management tools, and ticketing systems. This connection creates automated workflows for risk fixes, assessment, and stakeholder updates. Companies should use automation to handle complex IT environments that automatically find and assess digital assets.
Training teams and aligning with DevOps
Developers have an unmatched grasp of their applications. This makes them perfect for creating ASM security policies that fit specific needs and vulnerabilities. Training investments help teams stay current with the latest ASM tools and techniques. Security practices that line up with DevOps lead to better application protection through policy-based approaches and continuous improvement cycles.
Measuring and Improving ASM Performance
Clear metrics and testing systems must measure how well attack surface management works. Security investments need accountability and direction through measurable outcomes.
Key metrics: time-to-remediate, coverage, incident response
Critical severity vulnerabilities took 65 days to fix on average in 2023. CISA suggests a 15-day window for remediation. Teams should track these key performance indicators:
- Asset Coverage Rate: Percentage of assets under continuous monitoring
- Mean Time to Detect (MTTD): Duration between vulnerability appearance and discovery
- Mean Time to Remediate (MTTR): Speed at which teams fix confirmed exposures
Running red team exercises and audits
Red team exercises confirm how well attack surface management works by simulating real cyber attacks. These tests reveal gaps in detection, coordination and decision-making when teams are under pressure. We tested alerting, escalation and containment processes in real-life conditions. Teams document everything during exercises to preserve and act on lessons learned.
Feedback loops and continuous improvement
ASM needs constant updates through improvement cycles. Teams should add lessons from incidents and vulnerability checks into asset lists and fix processes. Looking at past trends helps learn about security's progress over time. This data helps teams spot bottlenecks, simplify processes and use resources well. Live monitoring helps security teams keep up with trends through proactive defense plans.
Conclusion
Attack surface management plays a critical role in modern cybersecurity strategies. Organizations with growing digital footprints need systematic approaches to find, classify, and monitor their external-facing assets. A complete mapping process shows both known and shadow assets, which builds reliable security foundations. Asset discovery acts as the first line of defense against potential attackers who look for overlooked entry points.
Security teams become more effective when they prioritize risks, especially with limited resources. Protection efforts should focus on high-value assets based on business effect, threat intelligence, and proven risk scoring frameworks. This strategy helps organizations put resources where they matter most instead of spreading them thin across all assets. Security teams can tackle the most critical vulnerabilities first, which reduces overall organizational risk.
ASM tools work better when integrated with existing security infrastructure throughout the enterprise. Security teams can create quick remediation processes that grow with attack surfaces by connecting ASM platforms to SIEM, SOAR, and ticketing systems automatically. Performance metrics like time-to-remediate and coverage rates offer vital feedback to improve continuously. Red team exercises also verify how well ASM works by testing systems under realistic attack conditions.
Organizations that use complete attack surface management move from reactive to proactive security positions. This change gives security teams the ability to stay ahead of emerging threats rather than just responding to breaches. ASM reduces successful cyber attack chances by removing blind spots and focusing on vulnerabilities based on real business risk. Setting up reliable attack surface management needs investment in tools and processes, but the protection against sophisticated cyber threats makes it essential for organizations of all sizes in today's digital world.
